5 Museum Collection Management Software Platforms With Public Exhibit Integration

Museums are magical places. But behind every beautiful gallery is a lot of hard work. Curators track objects. Registrars manage loans. Educators build exhibits. And now, visitors expect digital access too. That is where museum collection management software comes in. The best platforms do more than store data. They connect collections to public exhibits, websites, […]
7 Environmental Monitoring Software Tools Compared for Chemical, Biology, and Research Labs

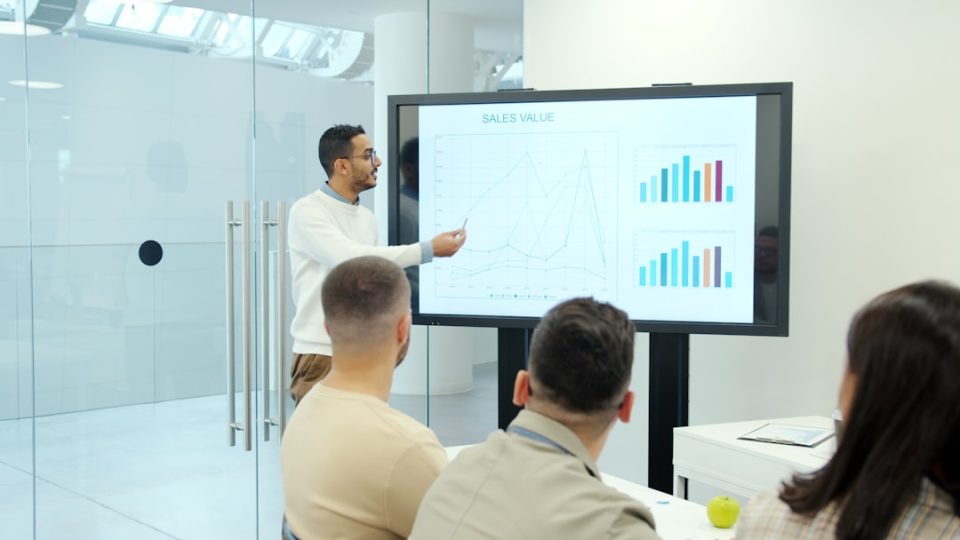
Environmental monitoring software has become a critical component of modern chemical, biological, and research laboratories. As regulatory demands tighten and quality standards evolve, laboratories must maintain precise control over temperature, humidity, air quality, differential pressure, and hazardous materials. Manual logging and fragmented systems are no longer sufficient. Today’s laboratories require integrated, auditable, and scalable solutions […]
Top 4 Pika Labs Tips to Turn Text Prompts Into Viral-Ready Social Videos

Ever seen a short AI video blow up overnight and wondered, “How did they even make that?” The answer is often simple: smart prompts and a few clever tweaks inside Pika Labs. You don’t need to be a filmmaker. You just need the right approach. In this guide, you’ll learn four powerful tips to turn […]
What Does 67 Mean In Slang? Full Explanation And Popular Uses Online

Numbers mean more than math online. They turn into jokes. They become secret codes. They even tell stories without using full sentences. One number that often makes people pause is 67. At first glance, it looks random. But in slang, it can carry different meanings depending on context. Let’s break it down in a fun […]
6 Final Cut Pro Editing Techniques That Speed Up Workflow for Mac Creators

Efficiency is the foundation of professional video editing. For Mac creators using Final Cut Pro, speed is not just a luxury—it directly affects turnaround times, creative momentum, and profitability. While powerful hardware certainly helps, mastering the right workflow techniques inside Final Cut Pro is what truly transforms performance. The following advanced yet practical methods will […]
5 Runway ML Tutorial Guides Every Creator Should Watch for AI Video Editing
AI video editing used to feel like science fiction. Now it’s something you can learn in an afternoon. Runway ML is one of the most exciting platforms leading this change. It helps creators turn simple ideas into stunning videos with just a few clicks. But like any powerful tool, it works best when you know […]
What Time Does Sonic Close Today? Hours, Locations, And Special Holiday Exceptions

Sonic Drive-In is famous for its carhops, slushes, and late-night burgers. But when hunger strikes, one big question pops up: What time does Sonic close today? The answer depends on where you are, the day of the week, and even the time of year. In this guide, we break it all down in a simple […]
3 DaVinci Resolve Workflow Tutorials for Beginners to Professional Projects

DaVinci Resolve has evolved from a high-end color grading application into a fully integrated post-production powerhouse used by YouTubers, indie filmmakers, and Hollywood studios alike. What makes it especially exciting is that the same software supports absolute beginners and seasoned professionals—without forcing you to switch platforms as your skills grow. Whether you’re cutting your first […]
Is SEC Network Available On YouTube TV? Subscription Options And Channel Access

The SEC Network has become a must-have channel for college sports fans, particularly those who follow Southeastern Conference athletics. With cord-cutting on the rise, many viewers are wondering whether they can access SEC Network through popular streaming services like YouTube TV. Understanding subscription options, channel availability, and potential add-ons is essential for anyone hoping to […]
Does YouTube TV Have NFL RedZone? Availability, Pricing, And Alternatives For 2026

For football fans who crave every touchdown, every Sunday, NFL RedZone has become nearly as essential as the games themselves. As streaming replaces traditional cable, many viewers are asking the same question in 2026: Does YouTube TV have NFL RedZone? The short answer is yes—but there are details about pricing, packages, and alternatives that are […]
